The Dark Side of Customer Data Protection: Why Trust Starts With Your CRM
Why Customer Data Protection Is a Leadership Responsibility — Not Just an IT Problem
Most business owners don’t think of themselves as custodians of sensitive data.
They think in terms of sales, customers, growth, marketing.
But the moment you store an email address, a phone number, or a customer note inside a CRM, you’ve taken on a responsibility that goes far beyond marketing performance. You’re now holding something that has real-world value (sometimes more than you realise) and not always to people with good intentions.
This article isn’t about scaring you. It’s about helping you understand why customer data is valuable, how it’s misused in the real world, and what “a trusted CRM” actually means in practice, without turning this into a technical lecture or a hacker’s handbook.
Why “just emails and phone numbers” still matter
A single email address on its own doesn’t feel dangerous. Neither does a phone number. The problem is that data rarely exists in isolation.
When customer contact details sit inside a CRM, they’re usually accompanied by:
- names
- enquiry history
- services used
- locations
- timestamps
- internal notes
- automated emails or SMS history
Individually, these details feel harmless.
Together, they create context, and that's what makes impersonation, phishing, and fraud believable.
That’s why customer contact data is often described as fuel.
It’s not always the end goal, but it enables far more damaging activity downstream.
How stolen customer data is actually used (without the Hollywood myths)
When people hear “stolen data,” they often imagine a lone hacker breaking into a system and immediately selling a spreadsheet online.
Reality is less dramatic and far more operational.
In most cases, misuse follows a pattern:
- Someone gains access: Often through stolen credentials, phishing, reused passwords, or overly broad access—not exotic exploits.
- Data is quietly extracted: CRM exports, synced marketing tools, or integrations do the heavy lifting.
- The data is monetised indirectly: Through scams, impersonation, account takeovers, or by selling access onward.
The uncomfortable truth is this that many data incidents succeed not because systems are “broken,” but because they’re trusted too much.
Who actually wants customer data?
It’s useful to think in terms of roles, not stereotypes.
- Bulk spammers and illegal marketers: They value scale. Lists of emails or phone numbers, especially when segmented, are used to run spam, scam SMS, or robocall campaigns.
- Phishing and social engineering operators: They care about realism. Even small details like a recent enquiry or familiar brand name dramatically increase success rates.
- Account takeover groups: They rely on email addresses to attempt password reuse across platforms—one breach often feeds many others.
- Business email compromise (BEC) fraudsters: These are among the most financially damaging actors. They impersonate staff or suppliers to divert payments, often using genuine internal context.
- Insider risk (intentional or accidental): Poor offboarding, shared logins, or unmanaged agency access mean data can “walk out” without any hacking at all.
None of these rely on genius-level skills. They rely on access, trust, and oversight gaps.
“How much is this data worth?” (and why that’s the wrong question)
People often ask what customer data sells for. The honest answer is: less than you think per record. A basic list of emails or phone numbers isn’t especially valuable on its own.
What increases value is:
- freshness
- accuracy
- segmentation
- added context (names, behaviour, history)
But focusing on resale value misses the real risk. For legitimate businesses, the true cost of data exposure usually shows up as:
- loss of customer trust
- churn
- operational disruption
- legal and regulatory obligations
- reputational damage that lingers long after the incident
That’s why regulators like the Information Commissioner's Office focus less on what data was worth and more on whether appropriate protections were in place.
Why CRMs are such attractive targets for data breaches
CRMs sit at the crossroads of identity, communication, automation and revenue. They’re powerful by design, which is exactly why they’re risky when poorly configured.
Common weaknesses I see repeatedly:
- Everyone has admin access “for convenience”
- Exports are unrestricted and unmonitored
- API keys and integrations are never reviewed
- Former staff or agencies retain access
- Logins rely on passwords alone, or weak MFA
None of these feel dramatic day to day.
Together, they create a quiet, persistent exposure.
What a “trusted CRM” actually means for customer data protection
A trusted CRM is not defined by its logo. It’s defined by the controls wrapped around it.
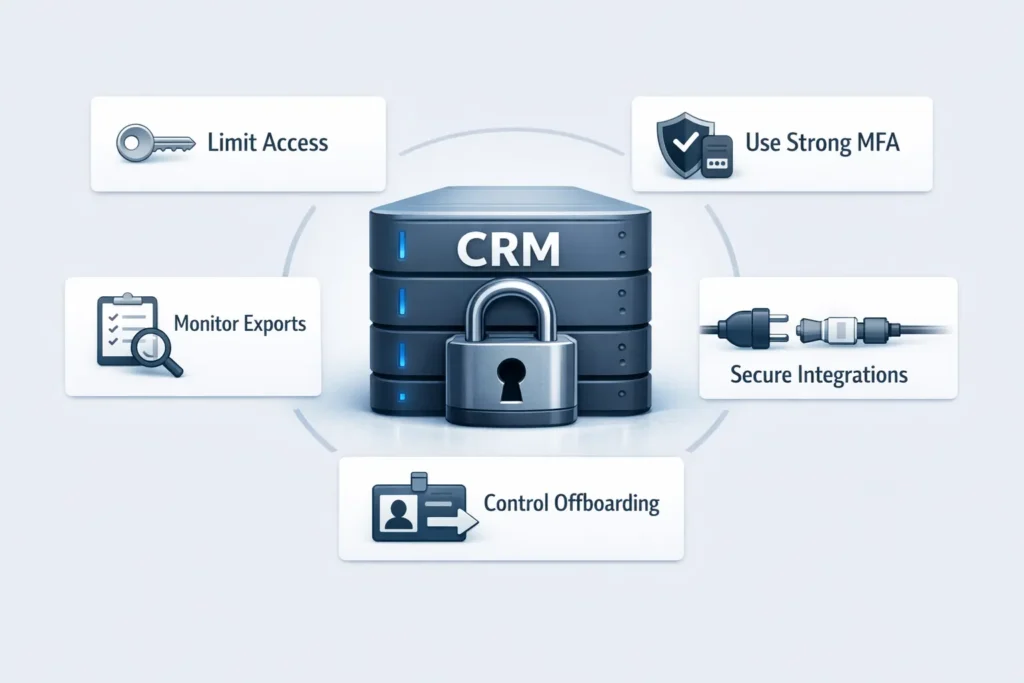
Identity and access controls
- Strong, phishing-resistant MFA for all users
- Role-based permissions (not everyone needs to see or export everything)
- Separate admin accounts for elevated access
- Single sign-on with conditional access where possible
The National Cyber Security Centre is very clear on this point: most breaches still start with compromised credentials.
Customer data protection and visibility
- Encryption in transit and at rest
- Clear restrictions on bulk exports
- Audit logs that actually show who accessed what—and when
- Alerts for unusual behaviour (new device + mass export is a classic warning sign)
Operational resilience
- Backup and recovery clarity
- Clear breach notification terms from vendors
- Regular security reviews—not just at onboarding
Trust isn’t about assuming nothing will go wrong.
It’s about being prepared when something does.
Well-known CRMs like Salesforce, HubSpot, and GoHighLevel all provide enterprise-grade security features. But those features only reduce risk if they are configured correctly, monitored, and governed properly.
Practical steps most businesses can take quickly
You don’t need an enterprise security team to reduce risk meaningfully. Do the following as a starting point to better customer data protection.
In the next 30 days:
- Enforce strong MFA across CRM, email, and finance tools
- Review who has export permissions
- Audit active users and integrations
- Turn on and retain audit logs
In the next 90 days:
- Introduce conditional access rules
- Implement regular access reviews
- Define a simple incident response plan
- Decide who is responsible for monitoring and escalation
Most serious incidents of a leak in customer data protection is due to not having any controls in place.
They fail because no one owned them.
Choosing the right partner (and the right questions to ask)
If you work with an agency, managed service provider, or systems partner, security should not be implied; it should be explicit.
Good questions to ask about customer data protection are:
- Who manages access when staff or contractors leave?
- Who reviews logs and alerts, and how often?
- What happens in the first 24 hours of a suspected breach?
- Can you help meet UK GDPR expectations if we need to report?
A partner who can’t answer these clearly is not managing risk, they’re deferring it.
Final thought: Trust is built quietly and lost quickly
Customers don’t see your CRM. They don’t know your access policies or security tools. What they do notice is when something goes wrong.
Strong customer data protection isn’t about paranoia or perfection. It’s about respecting the trust customers place in your business and earning it repeatedly through good systems and good decisions.
In working alongside IT and cybersecurity specialists such as MSP Labs, who support complex environments like schools, it becomes clear that many data incidents don’t start with advanced attacks, but with everyday access and configuration decisions.
Written by Jacques van den Wijngaerd,
Co-Founder & Director at Prosperitiv
Jacques has spent more than a decade working with SMEs across marketing, CRM systems, and automation; often at the intersection where growth ambitions meet data responsibility. His work focuses on helping businesses build scalable systems without sacrificing trust, security, or long-term credibility.
Recent Posts
Popular Posts
About us and this blog
We are a digital marketing company with a focus on helping our customers achieve great results across several key areas.
Request a free quote
We offer professional SEO services that help websites increase their organic search score drastically in order to compete for the highest rankings even when it comes to highly competitive keywords.